
Staff Augmentation Managed Securely: From Onboarding to Offshore Governance
Last year, a VP of Engineering called me after his offshore developer pushed AWS keys to GitHub. This happened at 2 AM. The keys stayed public for six hours before anyone noticed. That mistake cost $15,000 in cloud bills and three weeks fixing the damage. The real problem was not the money. It was trust. His board started asking if working with offshore teams was even safe.
I have worked on projects where new developers started writing code on their first day. I have also seen teams wait a month just to get basic access working. The difference was not the people. It was the process. When you bring offshore developers onto your team, you need clear rules for access, isolated workspaces, automatic security checks, protected data, and clean exits.
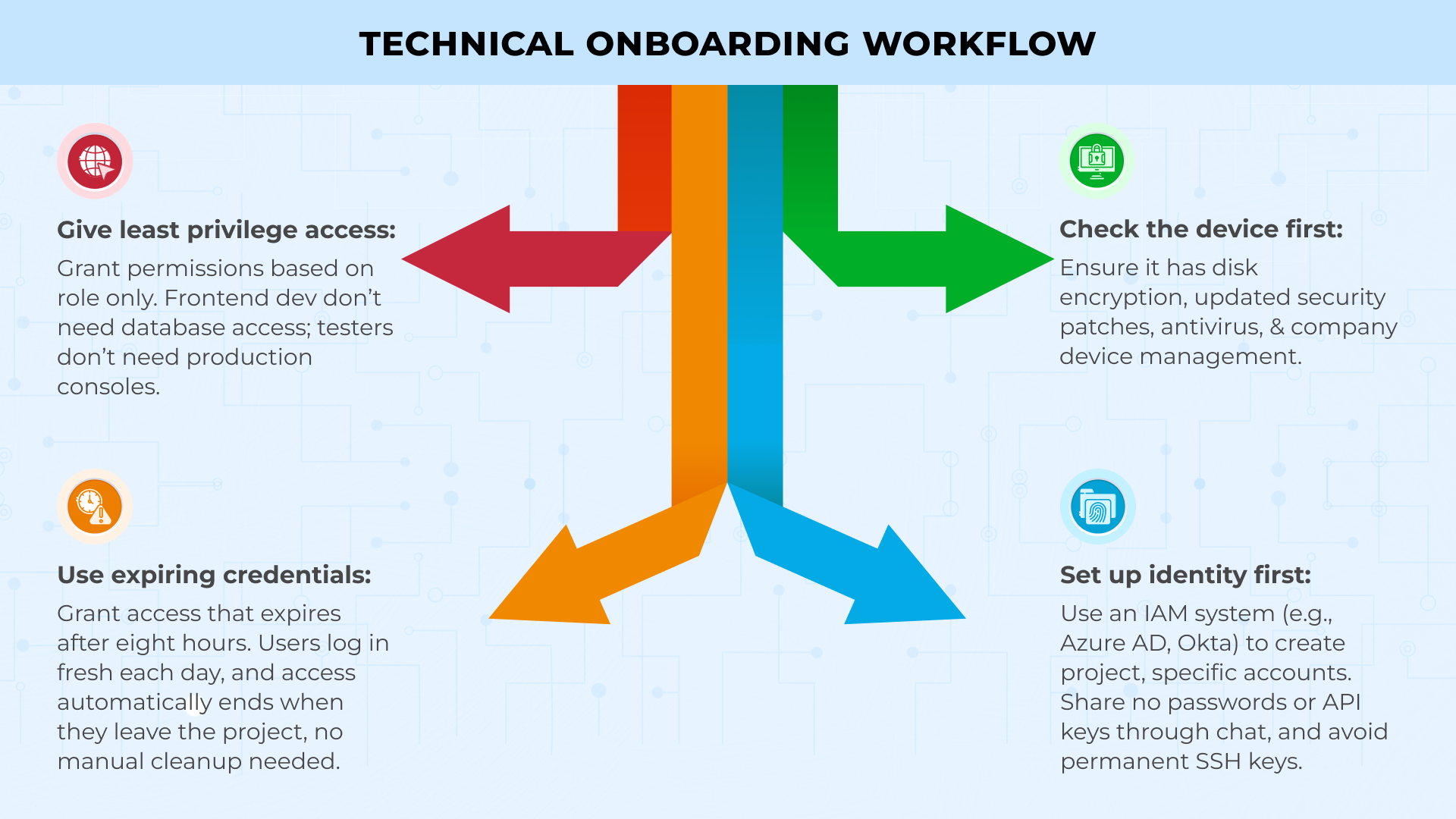
Technical Onboarding Workflow
Getting a new offshore developer started the right way matters more than anything else. If you are setting things up by hand each time, you are wasting time and creating security holes.
The best approach uses zero-trust principles. This means you trust nothing and verify everything. Every step would run automatically. And every permission would have clear limits and expiration dates. These are what you need:
-
Set up identity first
Use your identity and access management system to create accounts. Tools like Azure AD or Okta give out login details that only work for the specific project. No sharing passwords. No sending API keys through chat. No SSH keys that last forever.
-
Check their device
Before any code touches their laptop, verify the device is safe. It needs disk encryption, current security patches, antivirus software, and company device management. If the device fails these checks, access should be denied automatically.
-
Give minimum access only
Match their role to what they can see and touch. A frontend developer does not need database access. A tester does not need a production console. When someone joins your payments team, they get the payments code and test environment permissions. Nothing extra.
-
Use expiring credentials
Issue access that expires after eight hours. Every morning, they log in fresh. If they leave the project, their access stops on its own. No cleanup tickets.
This workflow can turn three weeks of waiting into 30 minutes of automated setup.
Development Environment Setup
Developers working on personal laptops is where secrets escape. Move them to isolated workspaces instead.
Use containerized environments to fix this. Set up GitHub Codespaces or Gitpod to create fresh workspaces from your code in about two minutes. Load each workspace with your base setup, all tools, code checkers, and security scanners.Here is how to set this up:
Configure your container environments:
-
Make workspaces temporary
Set them to delete after one hour of sitting idle. This keeps source code off personal computers and secrets inside your systems.
-
Load tools automatically
Pre-install dependencies, linters, and security scanners in every workspace. Developers open it, write code, commit changes, and close it. No local setup needed.
-
Control access through the cloud
Developers should only work in browsers or thin clients. They should never download your full codebase locally.
Build network layers next. Split access into three zones. Route public tools like Jira and Slack over the regular internet. Put software development and testing behind a protected network that checks IP addresses. Lock production behind a secure gateway that only opens during approved windows with temporary certificates.
Link network permissions to team groups in your IAM system. When you move someone from the frontend to the backend, their access updates automatically. No support tickets. No waiting.
The goal is simple. Make the safe path also the fast path. When spinning up a secure workspace takes two minutes and copying files to a desktop takes ten, people choose the secure option.
Code Quality & Security Pipelines
Catch security problems before code hits your main branch. Build checks into your development flow so they run on every push without anyone having to remember. Start with pre-commit hooks on developer machines. Install these to catch secrets, large files, and basic conflicts before anything leaves their workspace. This is your first line of defence.
Set up your CI/CD pipeline with four automated gates:
-
Run code security scanners:
Configure tools like SonarQube or Checkmarx to find unsafe patterns, SQL injection risks, and cross-site scripting holes in every commit.
-
Check dependencies for vulnerabilities:
Use automated scanners to flag third-party libraries with known CVEs. Block builds that use libraries with critical security issues.
-
Verify license compatibility:
Set up scanners to catch GPL or other incompatible licenses before they get into your proprietary code.
-
Scan container images:
Check that base images are current and patched. Reject any images with high-severity vulnerabilities.
Configure each gate to post results directly on the pull request. If any check fails, stop the entire build. No bypass option. No exceptions.
Build a dashboard that shows four numbers in real time. Test coverage percentage, critical findings count, average build time, and how long branches stay open. Make this visible to every team. Green will mean merge. Red will mean fix first.
Research shows 95% of data breaches happen because of human mistakes. And automated pipeline checks catch these mistakes before they cause problems.
Data Protection & Staff Augmentation
Different types of data need different levels of protection. You have to sort your data first, then apply the right controls to each type.
Use three categories:
-
Public data:
Moves freely without restrictions. Marketing content, public documentation, open-source code.
-
Confidential data:
Business plans, proprietary code, and customer lists need encryption at rest and in transit. Limit access to employees who need it for their work.
-
Regulated data:
Stays locked in monitored areas with detailed logs. Patient health records, payment card numbers, and social security numbers.
IBlock offshore developers from accessing real customer data during development. Give them synthetic data instead. Generate fake names, addresses, and IDs that look real but contain zero actual customer information. Or use data masking tools that replace sensitive fields while keeping the data structure intact. A healthcare app keeps real diagnosis codes and dates but swaps in fake patient names and medical record numbers.
Push endpoint controls through MDM when contractors join. Turn on disk encryption, add screen watermarks to sensitive pages, and activate cloud access policies that block copying to personal drives. Block screenshots on confidential documents. If someone tries to exfiltrate data, the system blocks them at the device level.
The numbers tell the story. Average data breach costs hit $4.88 million in 2024. Every piece of unprotected data is a potential million-dollar problem.
Communication with Clients
Clear communication keeps offshore projects running smoothly. Always set up your communication tools and schedules before work starts.Configure your communication tools first:
-
Run daily standups over encrypted video:
keep them to fifteen minutes. Each person should share what they finished yesterday, what they are working on today, and what is blocking them. Record every call and store recording in systems you own. Never in contractor accounts.
-
Schedule weekly security reviews:
Use shared documents that timestamp every edit. Cover threat models, new vulnerabilities, and upcoming security work in each review.
-
Hold monthly demos from your repositories:
Pull code from your systems only. And never from copies sitting on contractor servers.
Control all project communications:
Create Slack or Teams workspaces under your company account. Give offshore team members guest access that you control. When projects end, revoke their access and keep all message history.
Always post metrics where everyone can see them. Build success rates, test coverage, and security scan results. When a security gate blocks a merge, the reason displays automatically. No one needs to ask why.
This transparency makes offshore teams feel like real partners, not vendors.
Compliance
Build compliance into your process from day one, not as paperwork you add later. Map controls to frameworks before audits. SOC 2 needs access reviews and encryption. ISO 27001 adds risk assessments. GDPR requires data agreements and breach procedures. PCI DSS covers payment data with network segmentation.
Create a simple matrix. Rows show security controls. Columns show compliance frameworks. Mark which requirements each control satisfies. Store this in version-controlled documents.
Write controls in plain language. Say “Credentials expire after 8 hours”, not “time-bound access provisioning protocols.”
Your systems already create evidence. IAM logs track access. Pipelines record scans. Monitoring shows data queries. Always collect these in one place.
Stats back this up. 50% of businesses faced a security breach in the past year. Having controls documented before breaches happen shows auditors you take security seriously.
Case Study Scenario
Look at how Parakeet handled this. They needed PCI Level 1 compliance for their B2B payments platform to work with Visa, Mastercard, and American Express.
They brought in specialized DevOps partners and hit full compliance in 6 weeks. Three times faster than doing it alone. The team used containerized workloads on Amazon EKS with automated pipelines. Nothing reached production without approval and testing.
AWS security services handled intrusion detection, encryption, monitoring, and attack prevention as one coordinated system.
The results were: Production launch in under 3 months. Avoided hiring two cloud engineers, saving $200,000 yearly. Cut cloud costs by 53% on dev and test environments. PCI compliance opened the Xero partnership and expanded their customer base.
Security governance speeds delivery when built in from the start.
Conclusion
Build security into your staff augmentation process from the start. Do not add it later as an afterthought.
Set up three foundations first. Use identity and access management for all logins and permissions. Deploy containerized environments for development work. Install automated security checks in your build pipeline.
These three steps stop most security problems before they happen.
Add monitoring tools next. Set up clear communication channels. Create clean offboarding workflows that revoke access automatically when contracts end.
At Telliant Systems, we help teams implement these processes across healthcare, finance, and enterprise software. Technical controls and governance rules work together so offshore development becomes your advantage.
When it’s done right, secure offshore teams move faster than traditional hiring because safety is built into speed.






































