
Ensuring Data Security in Software Development: Best Practices
Data security matters now more than ever in software development. More data is being stored, transferred, and utilized by apps than ever before, attackers are better and faster than ever, cloud and third-party APIs make up a large part of most codebases, and nearly all companies – no matter how tech-adjacent – now have some kind of online presence.
With so much surface area, and with devs producing code faster than ever, security breaches are bound to happen. Baking security into your code and development lifecycle is critical to stay ahead of the curve. In this article, we’ll look at how to build in data security, best practices and techniques, and privacy and regulatory concerns.
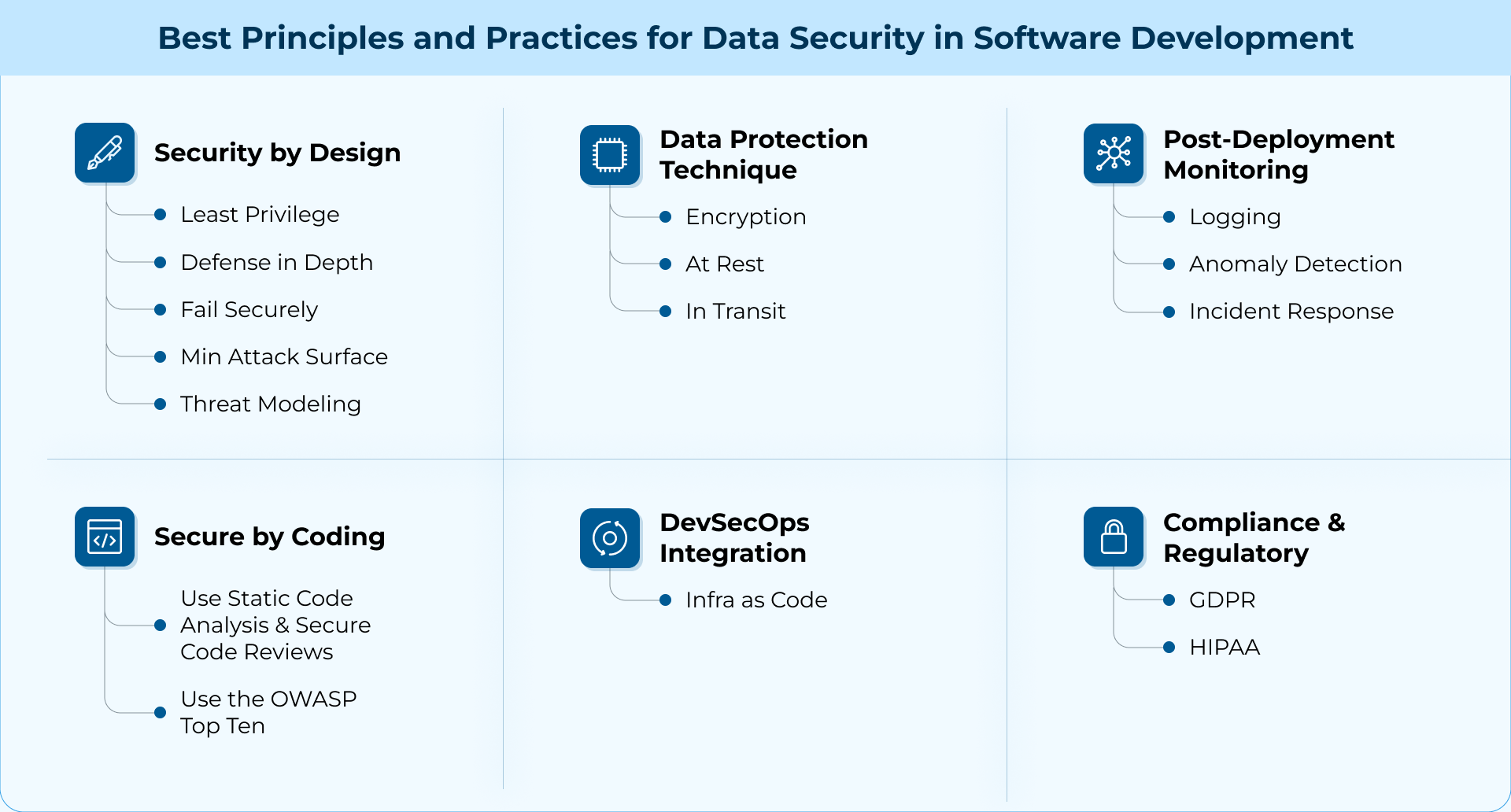
Best Principles and Practices for Data Security in Software Development
1. Security by Design
The most secure software has security wired in by default – not tacked on after the fact. Threat modeling and risk assessment should be done early in the Software Development Lifecycle (SDLC) to ensure adherence to best practices and principles.
Here are the principles your business should strive to achieve:
-
Least Privilege
Every component of the system – whether that’s the user, a module, a process – should have access to only the minimum it needs to do its job. This limits the blast radius in case of a compromise.
-
Defense in Depth
A single layer of security isn’t enough: you need layers of input validation, firewalls, encryption, monitoring, so that if one fails, the others are there for backup.
-
Fail Securely
Don’t return detailed error messages that allow attackers to guess credentials or ever share credentials in failstates.
-
Minimize Attack Surface
Every API, endpoint, login, and connection is a potential security breach. Only expose what is absolutely necessary and never make the default state an insecure one.
-
Threat Modeling
Think like an attacker – and have your devs think like attackers when they write code. And don’t just do this once, do it for every new module you build.
2. Secure by Coding
There are some core best practices you can implement to ensure that the code you’re writing is secure. Let’s take a look at a couple of those practices.
-
Use the OWASP Top Ten
The OWASP Top Ten is a security vulnerabilities list maintained by the Open Worldwide Application Security Project. It’s regularly updated with the most commonly seen and most critical security risks faced by software applications.
Checking this list before and during development is a good idea to stay on top of changing requirements. Here is a quick rundown of the current (as of 2021) list:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-Side Request Forgery (SSRF)
-
Use Static Code Analysis and Secure Code Reviews
Static code analysis is the process of analyzing code without running it. Usually, this is done by a tool that scans your code for risky patterns. This is different from running a test suite, which actually exercises your code paths – it just looks for things like hardcoded credentials, SQL queries that use direct user input, or functions that disable SSL checks.
Code reviews are a similar process, but performed by a human. Every pull request opened against a repository should be checked by a human pair of eyes, ideally a pair of eyes familiar with the codebase and with security best practices.
3. DevSecOps Integration
CI/CD (Continuous Integration/Development) allows you to iterate on and ship code quickly – but it’s important to make sure that that speed doesn’t come at the cost of your app’s security. Luckily, DevOps is one place where security can be truly automated and baked right into the development process.
Processes like dependency scanning, Static Application Security Testing (SAST), secret detection, Infrastructure as Code (IaC) scanning, and container image scanning are all automated things that can catch issues before deployment.
- Infrastructure as Code
Infrastructure as Code is a smart new way to spin up apps on cloud services and platforms like AWS. Rather than logging in and clicking around to create instances through the UI, you can write config files that spin up all the necessary services for you.
This is a major security improvement, because it’s repeatable, scannable (the infrastructure code itself can be scanned for implementation issues), requires no auth or login, and allows for version control.
4. Data Protection Techniques
Let’s talk about two primary data protection techniques that every app needs to manage to maintain security at the most basic level: encryption (at rest and in transit) and secret management/access control.
-
Encryption
Encryption means scrambling data so it’s unreadable (either by humans, or by outside processes.) There are two moments when data encryption occurs: at rest (i.e. while the data is static) and in transit (i.e. when it’s being sent across the network.)
-
At Rest
All data should be encrypted when it’s stored – in an S3 bucket, in your database, on a hard drive, etc. That way, if a bad actor gains access to the data, it’s still safe. Some common examples of how to encrypt data at rest are:
- Database storage encryption (e.g., AWS RDS encryption)
- Disk-level encryption (e.g., LUKS on Linux, BitLocker on Windows)
- Encrypted object storage (e.g., S3 server-side encryption)
-
In Transit
Once the data leaves its storage location and makes its way across the network, it needs a different form of encryption in case it’s intercepted. A few ways you can do this to prevent things like Man-in-the-Middle attacks are:
- HTTPS for web traffic
- TLS for internal service-to-service communication
- VPNs or SSH for secure network tunnels
5. Compliance and Regulatory Considerations
In the last ten years, the world has become more security-savvy and privacy-aware. Users expect secure services now, and data breaches are massive blows not just to a business’s back end, but to their brand and credibility. Governments have implemented compliance and industry regulations that need to be strictly followed.
-
HIPAA
The Health Insurance Portability and Accountability Act is the primary regulation applying to US-based healthcare providers and insurance companies. It requires data confidentiality (ensuring personal health data is only available to authorized users), data integrity, audit controls, access controls, encryption, and Business Associate Agreements (BAAs) with third parties.
-
GDPR
The General Data Protection Regulation applies to EU countries, and to any company that handles the data of EU residents. It requires explicit user consent, right to access and erase data, minimization of data collection, and breach notification.
6. Post-Deployment Monitoring
During the post-deployment phase of development, you need to be thinking about logging, anomaly detection, and incident response.
-
Logging
Using a centralized logging system to track system events will make tracking down the root cause of a breach faster and easier (and will allow you to prevent future breaches.) Without logging, your devs are flying blind in the event of a data breach.
Platforms like ELK, Datadog, and AWS CloudWatch can support your logging efforts. You should make sure that logs include timestamps, user IDs, and context – and make all logs tamper-resistant.
-
Anomaly Detection
Anomaly detection allows you to detect irregular patterns quickly – sometimes alerting you to a breach before it even happens. Examples of unusual or suspicious behavior might be:
- A user logging in from two countries 30 minutes apart
- A spike in 500 errors on an API that’s usually quiet
- A database query pulling more rows than usual
-
Incident Response
You need a structured, documented, and repeatable plan for responding to problems when they arise. Prepare this plan during the planning phase of development – don’t wait until you’re in the middle of a data breach to start figuring it out!
Conclusion
As attack surfaces grow and software gets more interconnected, the cost of neglecting security rises fast. It isn’t just a backend concern or something you tag on at the end of a sprint. It’s a mindset — one that needs to be present from planning to deployment to post-launch.
The good news is, building secure software isn’t about perfection — it’s about consistency, awareness, and making smart choices. The software product development teams that treat security as part of their core development culture, not just a checkbox, are the ones best positioned to build trust, protect users, and weather whatever comes next.






































